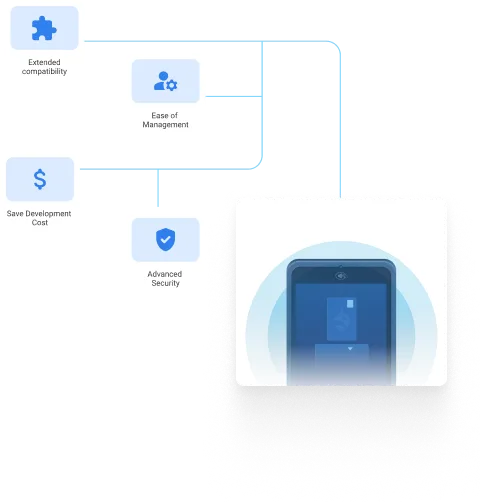
All-In-One MDM Platform Unified Management, Trusted Protection,
Unified Management, Trusted Protection,
and Effortless Compliance
Unified endpoint management, protection, and compliance for devices across all platforms.
Book a Demo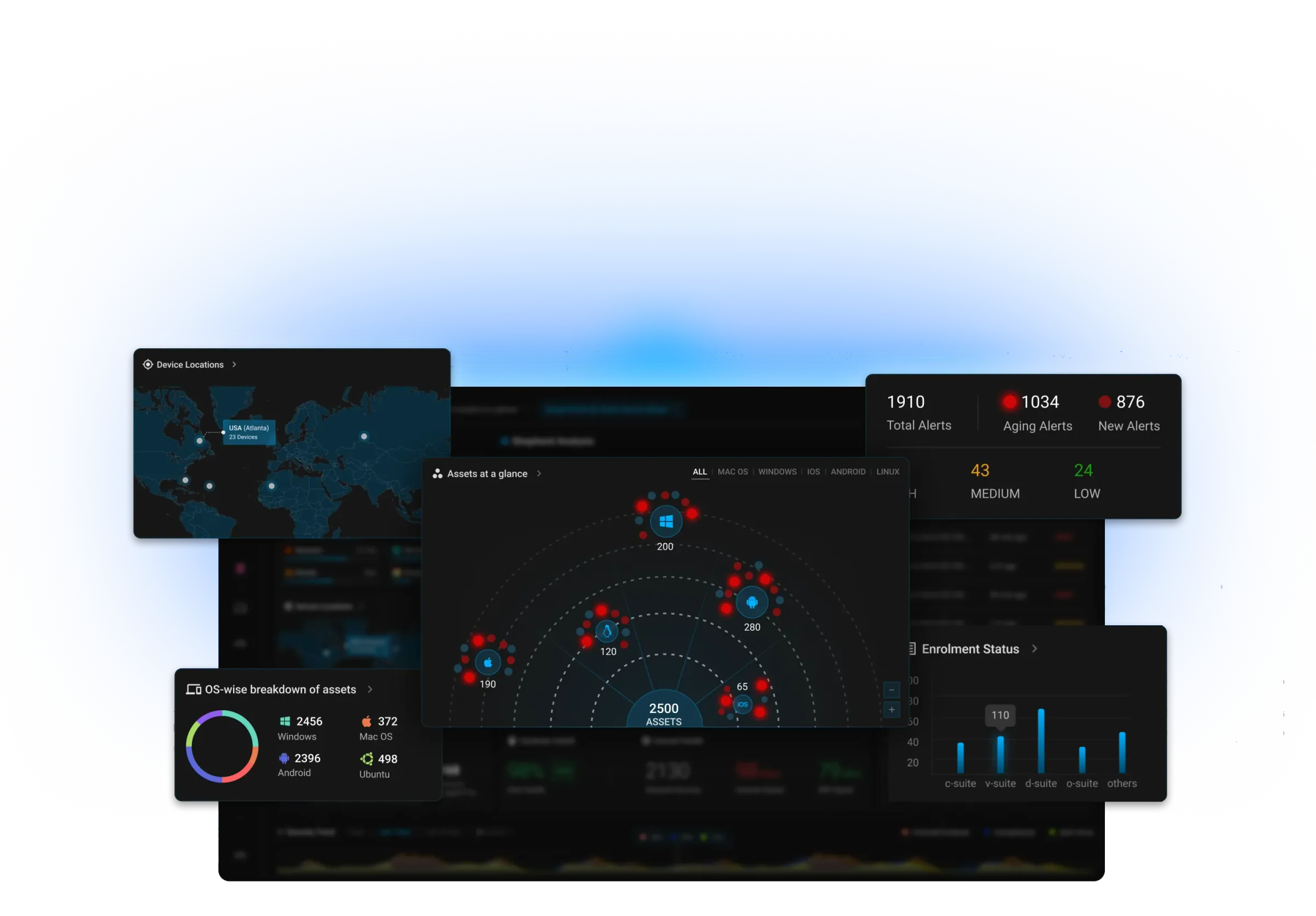

An All-In-One Solution For Managing, Securing,
and Optimizing All Devices.
Discover Shepherd
Explore Shepherd's Full Potential
Effortless implementation. Single pane of glass, one-click management for all products
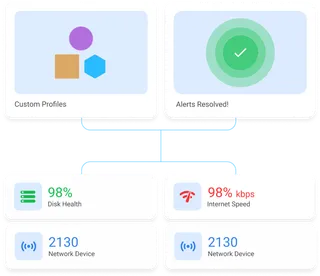
Active Device Management
Effortlessly provision, monitor, and control endpoints and applications in real-time.
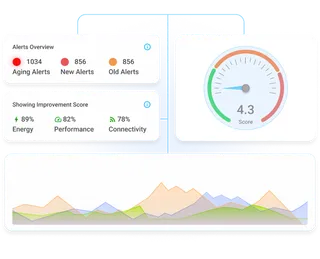
Active Performance Management
Gather deep-observability on hardware and application performance of each endpoint. Enforce actionable insights to optimize performance and productivity.
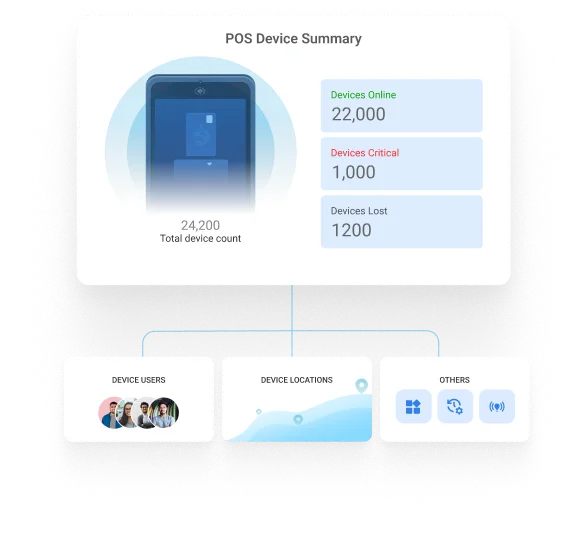
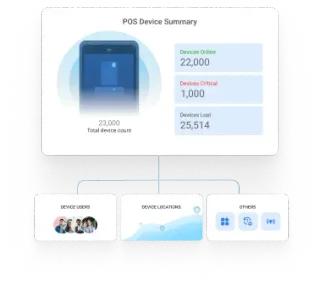
Active POS Management
Effortless device management and uptime enhancement across heterogeneous handheld and mounted POS devices.
Rugged Device Management
Deploy effortlessly across heterogeneous purpose-driven devices and make managing rugged devices a cakewalk.