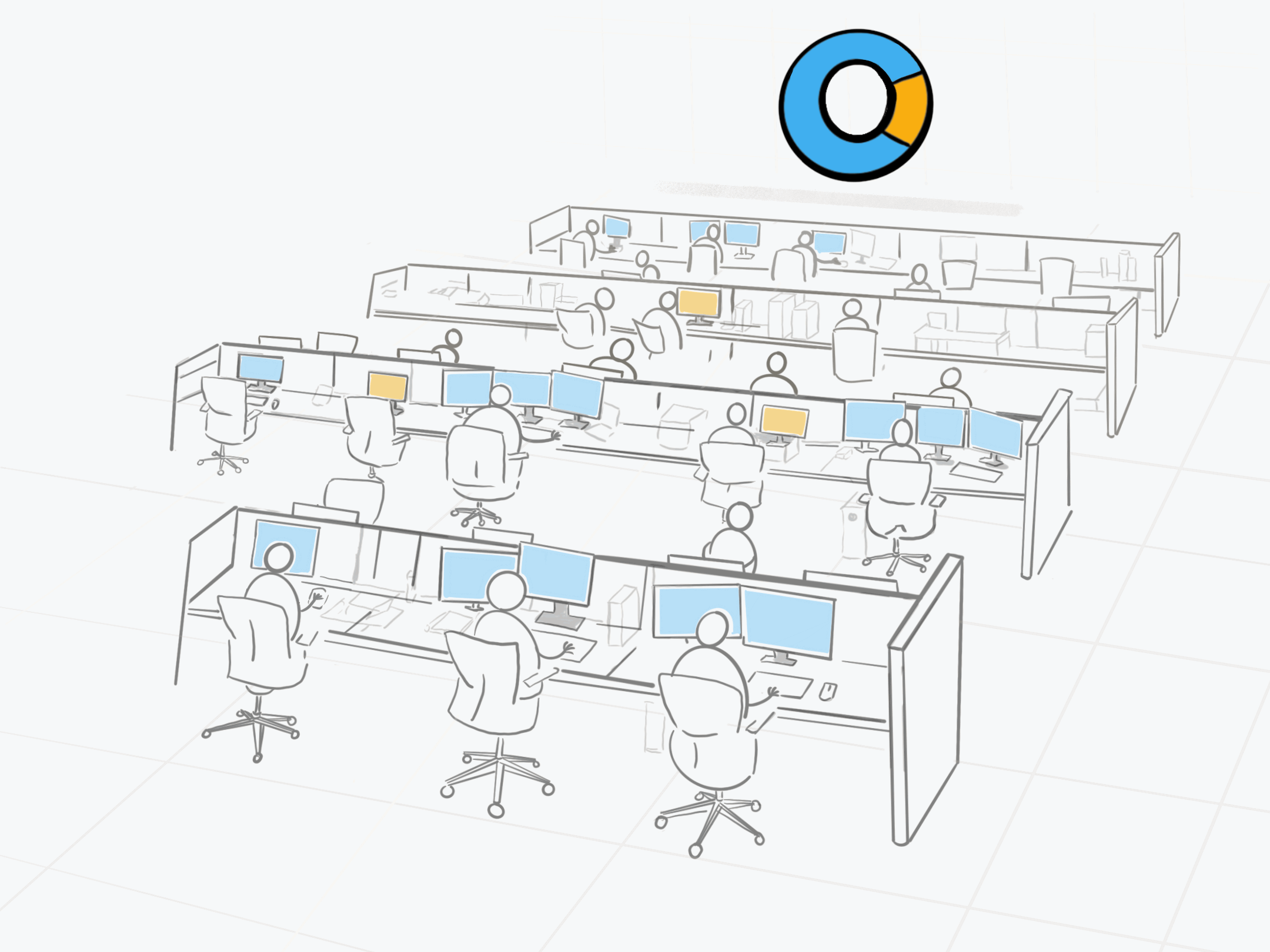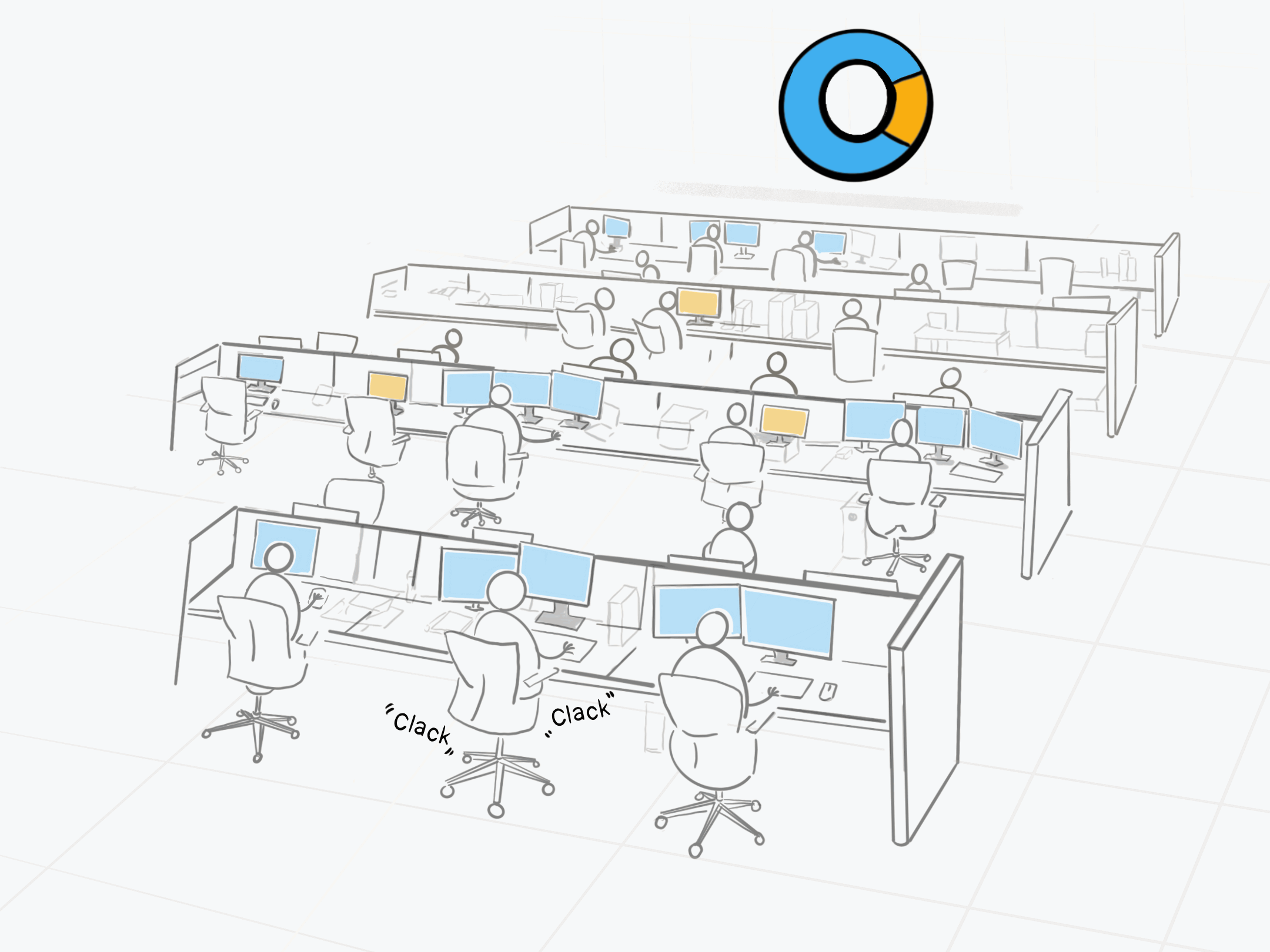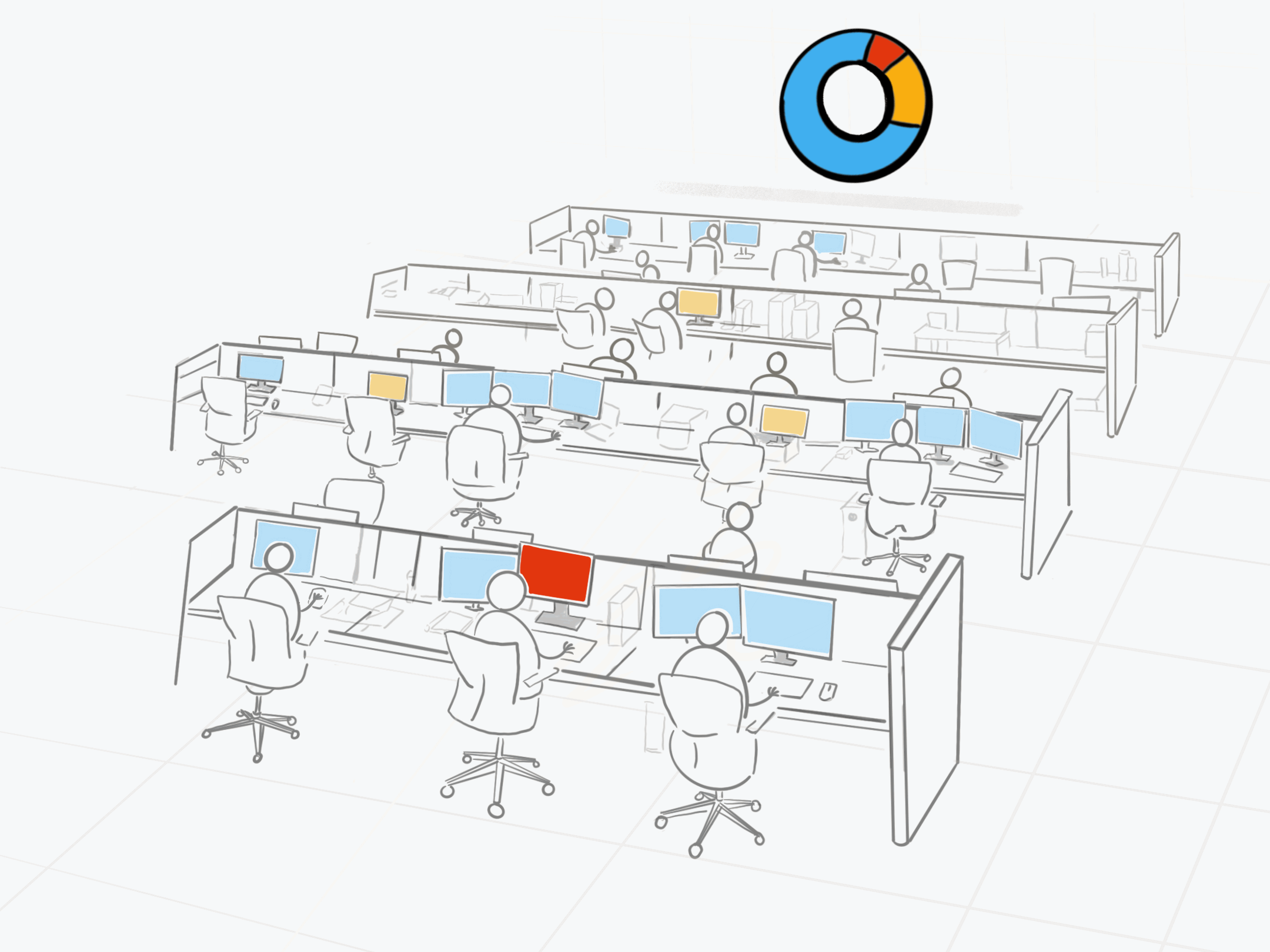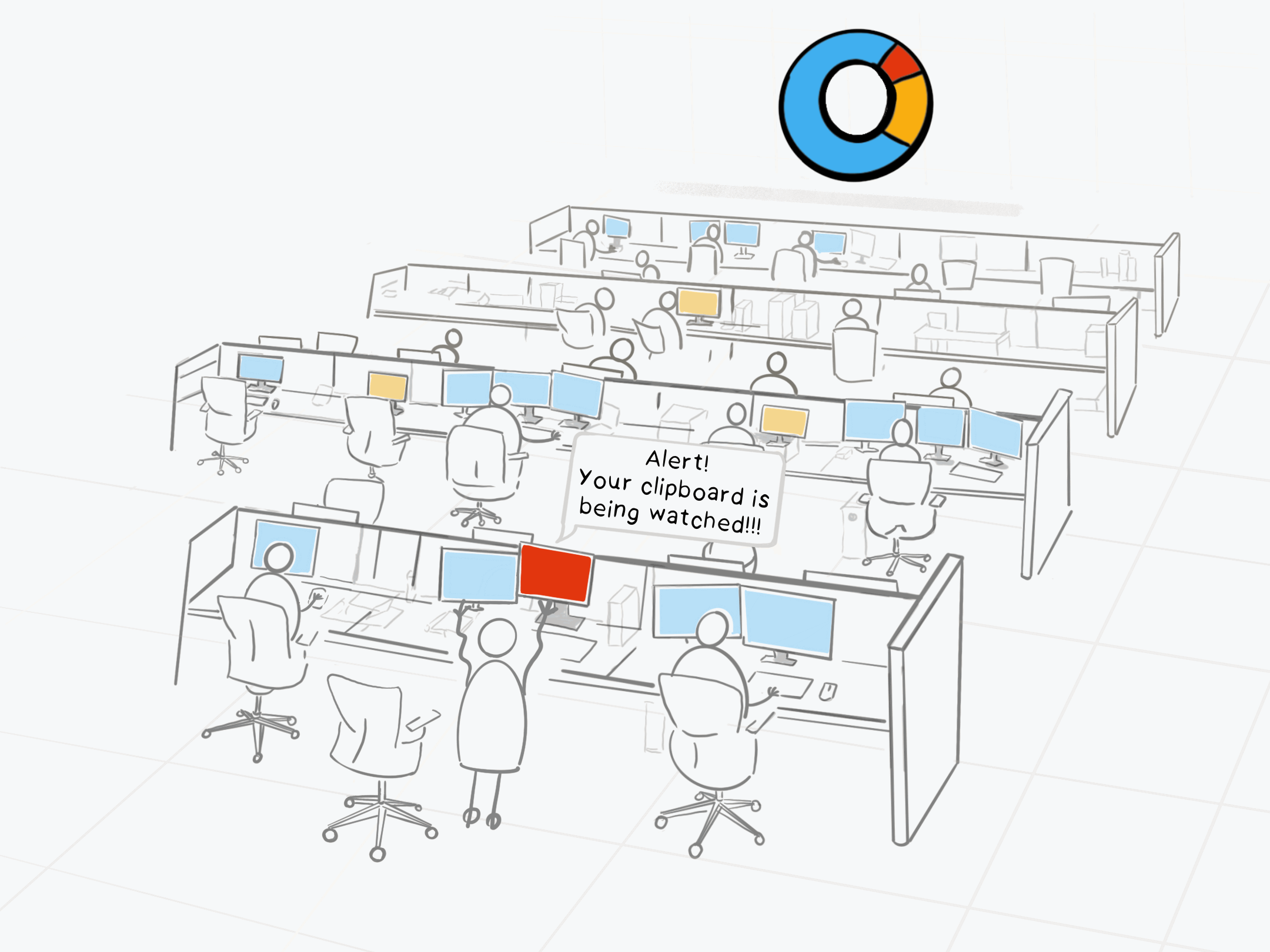
End-Users and Endpoints are the Weakest Links
in the Cybersecurity Chain
and implement recommended actions to harden its security in real time.
security posture of your endpoints. All at the endpoint, in near real-time!
Stay Ahead
Stay Ahead
Move Over ‘Reactive’ Defense
Adopt a proactive, ML -based defense for your devices and data with minimal manual intervention.
Say No To Sluggish Endpoints
Unlike existing solutions, we take up a smaller fraction of the resources to deliver performant defense in real time.
Embrace A Culture of Assurance
Allow our automation to protect your devices and data as you focus on your core comptencies

Anter Virk
CEO

Dilawar SinghCTO
Ph.D. Computational Neuroscience - NCBS Bangalore, Masters in VLSI Technology